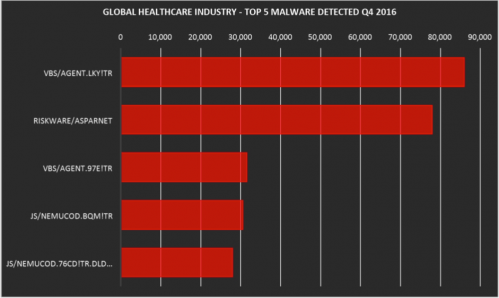
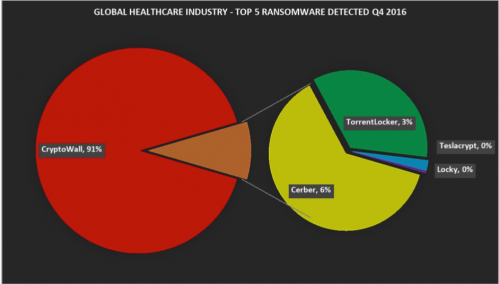
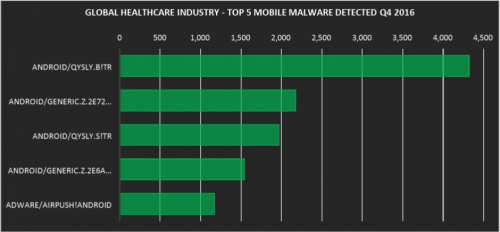
As long as the data has its value, the threat is always accompanied. In recent years, the threats facing the medical industry have become increasingly severe. The importance of data such as cases is self-evident, but relative to the financial industry, the investment in safety in the medical industry needs to be further improved. We will focus on the five major malware, ransomware, mobile malware, IPS events, botnets, and penetration code toolkits detected in the global healthcare industry in the fourth quarter of 2016. This provides industry-based threat situational awareness and suggests multi-dimensional security defenses. Five major malware Most of the five detected malware are known for being the initial attack vectors for ransomware attacks, while the top-level attack comes from the VB script-based dropper trojan (VBS/Agent.LKY!tr), which can be attacked. The second stage of downloading ransomware. Ranked second is "Riskware/Asparnet", a type of software that is usually unintentionally installed and secretly collects sensitive information without the user's knowledge. The remaining malware in the list is also considered to be the droppers Trojan ransomware (VBS/Agent.97E!tr, JS/Nemucod.BQM!tr and JS/Nemucod.76CD!tr.dldr). JS/Nemucod (and its variants) is a well-known JavaScript-based malware family that spam targets devices and downloads unwanted malware (mainly ransomware) to a personal computer. For example, an email is populated with a target device via a typical Nemucod spam with an encrypted JavaScript attachment. After decrypting the JavaScript, we can see that it is trying to download files from a hacker-controlled website to a user's temporary folder. The downloaded file is an executable file that is later used to encrypt the user's file. Five ransomware The most active ransomware we observed was CryptoWall, which accounted for more than 90% of all detected ransomware infections. Like most types of ransomware, CryptoWall hijacks the victim's data, encrypts the file, and asks for a ransom to decrypt the file. The malware displays a message telling the victim that their files have been encrypted and that they must pay the ransom within a limited time, otherwise the ransom will increase. In order to hide their identity to the fullest extent, malware authors use the Tor network and require lents payments in bitcoin, and we note that this trend is becoming more common. Ranked second is Cerber, and the detected infection rate is around 5%. Cerber has almost the same ransomware features as CryptoWall. TorrentLocker, TeslaCrypt and Locky are the other ransomware we have detected and are common in other industries. Five mobile malware Malware for Android dominates the top five mobile malware rankings. This may be because Android devices typically allow users to easily install applications from third parties that may be accompanied by malware based on Android. Fire Extinguisher,Domestic Fire Extinguisher,Electrical Fire Extinguisher,Arine Fire Extinguisher DONGGUAN TENYU TECH.INC , https://www.tenyutech.com